AWS Cloud Server Pricing Models
Understanding AWS pricing is crucial for effectively managing cloud costs. AWS offers a variety of pricing models, each designed to suit different usage patterns and budgetary needs. Choosing the right model can significantly impact your overall expenditure. This section will delve into the specifics of these models, focusing on Amazon EC2 instance pricing and strategies for optimization.
Amazon EC2 Instance Pricing Comparison
Amazon EC2 instances are categorized by instance type, which reflects the CPU, memory, storage, and networking capabilities. Pricing varies significantly across instance types, reflecting their performance characteristics. For example, a compute-optimized instance like a c5.large will cost less than a memory-optimized instance like an r5.large, even if both have similar CPU cores, due to the differing memory configurations. Similarly, instances with higher processing power and greater storage capacity will command a higher price. It’s important to select the instance type that best matches your application’s requirements to avoid overspending on unnecessary resources.
Cost Optimization Strategies for AWS Cloud Servers
Effective cost optimization is vital for maintaining a sustainable cloud infrastructure. Several key strategies can significantly reduce expenses. These include right-sizing instances (choosing the smallest instance that meets performance needs), utilizing reserved instances for predictable workloads, leveraging spot instances for fault-tolerant applications, and employing automation for resource management. Regular monitoring of resource usage and proactive scaling are also essential. Failing to properly monitor and manage your AWS resources can lead to unexpected and potentially substantial cost overruns.
Cost-Effective Infrastructure Plan Using AWS Spot Instances
AWS Spot Instances offer significant cost savings by providing spare EC2 compute capacity at a significantly reduced price compared to On-Demand Instances. However, Spot Instances are subject to interruption with a two-minute notice, making them unsuitable for applications requiring continuous uptime. To design a cost-effective infrastructure using Spot Instances, applications must be designed with fault tolerance in mind. This typically involves techniques such as using auto-scaling groups to automatically launch replacement instances when a Spot Instance is interrupted, and implementing mechanisms for data persistence and recovery. For example, a stateless web application with data stored in a persistent database would be an ideal candidate for a Spot Instance-based infrastructure. The application can be easily restarted on a new instance with minimal disruption.
Comparison of On-Demand, Reserved, and Spot Instances
| Instance Type | Pricing Model | Uptime Guarantee | Cost |
|---|---|---|---|
| On-Demand | Pay-as-you-go | Continuous | Highest |
| Reserved | Upfront payment or partial upfront payment | Continuous | Medium (discounted based on commitment) |
| Spot | Auction-based | Interruptible (2-minute notice) | Lowest |
AWS Cloud Server Security Best Practices
Securing your AWS cloud server is paramount to protecting your data and applications. A robust security strategy involves a multi-layered approach, encompassing preventative measures, detection mechanisms, and incident response planning. This section details essential security hardening techniques and best practices for AWS EC2 instances, focusing on network security and data protection.
Security Hardening Techniques for AWS EC2 Instances
Implementing security hardening involves strengthening the operating system and applications running on your EC2 instances to minimize vulnerabilities. This includes regularly updating the operating system and applications with the latest security patches, disabling unnecessary services and ports, and using strong passwords and access control mechanisms. Employing a strong baseline configuration, regularly reviewed and updated, is crucial. For example, disabling root login via SSH and using SSH keys for authentication significantly reduces the risk of unauthorized access. Furthermore, regularly scanning for vulnerabilities using automated tools and actively monitoring security logs helps detect and respond to potential threats promptly.
Implementing Security Groups and Network ACLs
Security Groups act as virtual firewalls for your EC2 instances, controlling inbound and outbound traffic based on rules you define. Network ACLs provide an additional layer of security, filtering traffic at the subnet level. Effective use of both is crucial. For instance, a Security Group might allow SSH access only from specific IP addresses, while a Network ACL could block all inbound traffic to a subnet except for specific ports required by applications within that subnet. Careful configuration is vital; overly permissive rules can significantly weaken your security posture. Regular review and refinement of both Security Groups and Network ACLs are essential as your infrastructure evolves.
Securing Data at Rest and in Transit
Data security encompasses both data at rest (stored on your EC2 instances) and data in transit (moving between your instances and other systems). Securing data at rest involves using encryption technologies like Amazon EBS encryption or encrypting files on the instance itself. For example, using AWS KMS (Key Management Service) to manage encryption keys enhances security and control. Securing data in transit involves using protocols like HTTPS for web applications and VPNs for remote access. Implementing TLS/SSL encryption for all communication channels is critical for protecting sensitive data from interception.
Comprehensive Security Plan for AWS Cloud Server Deployment
A comprehensive security plan should address all aspects of your AWS cloud server deployment. This includes defining clear security responsibilities, establishing a robust access control model using IAM roles and policies, regularly backing up data, and implementing a disaster recovery plan. A well-defined incident response plan is also crucial, outlining steps to be taken in case of a security breach. This plan should include procedures for identifying the breach, containing the damage, eradicating the threat, and recovering from the incident. Regular security audits and penetration testing help identify and address vulnerabilities before they can be exploited. This proactive approach is essential for maintaining a secure cloud environment.
AWS Cloud Server Deployment and Management
Deploying and managing AWS cloud servers, specifically EC2 instances, involves a straightforward yet powerful process. Understanding this process is crucial for efficiently leveraging the scalability and flexibility of the AWS cloud. This section details the key steps involved, from launching an instance to managing it using AWS Systems Manager.
Launching an EC2 Instance
Launching an Amazon EC2 instance begins in the AWS Management Console. Navigate to the EC2 service. You’ll then select “Launch Instance,” which presents you with a series of choices. These choices include selecting an Amazon Machine Image (AMI), defining instance type (based on processing power, memory, and storage needs), choosing a key pair (for secure SSH access), configuring storage (including the size and type of your root volume), and configuring a security group (to control network access). After reviewing your choices, you launch the instance, and AWS provisions the resources necessary. The instance then enters a “pending” state before transitioning to “running” once fully provisioned.
Configuring and Managing an EC2 Instance
Once your EC2 instance is running, several configuration and management tasks are essential. These include connecting to the instance via SSH using your key pair, installing necessary software packages, configuring the operating system, setting up user accounts, and implementing necessary security measures. You’ll also need to monitor the instance’s performance, ensuring it meets your application’s requirements. Regular updates and patching are crucial to maintain security and stability. AWS provides tools like CloudWatch for monitoring and logging, allowing you to track resource utilization, identify potential issues, and optimize performance.
Using AWS Systems Manager for Remote Server Management
AWS Systems Manager (SSM) offers a centralized control plane for managing multiple EC2 instances. It simplifies tasks like patching, software deployment, and configuration management. SSM allows you to execute commands remotely on your instances, simplifying administration. For instance, you can use SSM to install updates on multiple servers simultaneously, ensuring consistency and minimizing downtime. Its automation capabilities streamline repetitive tasks, improving operational efficiency and reducing the risk of human error. SSM also facilitates inventory management, providing a comprehensive view of your EC2 instance configurations and resources.
Deploying a Web Application on an AWS EC2 Instance
Deploying a web application on an EC2 instance involves several steps. First, you choose an appropriate AMI, such as one pre-configured with a web server like Apache or Nginx. After launching the instance and connecting via SSH, you’ll install any additional required software and dependencies. Next, you transfer your web application files to the instance, typically using tools like `scp` or `rsync`. Then, configure the web server to serve your application. This might involve creating virtual hosts or configuring reverse proxies, depending on your application’s architecture. Finally, you configure your security group to allow inbound traffic on port 80 (HTTP) or 443 (HTTPS), enabling external access to your web application. Throughout this process, using tools like Ansible or Chef for automation can greatly streamline deployment and improve consistency. Regular testing and monitoring are vital to ensure the application’s performance and stability.
AWS Cloud Server Scalability and High Availability

Building scalable and highly available applications on AWS requires careful planning and the strategic use of several services. This section details strategies for achieving both scalability, the ability to handle increasing workloads, and high availability, ensuring continuous operation even in the face of failures. We will explore key AWS services that facilitate these critical aspects of cloud-based application architecture.
Strategies for Scaling an AWS Cloud Server Application
Scaling an application involves adjusting its resources to meet fluctuating demand. This can be achieved through vertical scaling (increasing the resources of existing servers, such as CPU, memory, and storage) or horizontal scaling (adding more servers to distribute the workload). Vertical scaling is simpler but has limitations; horizontal scaling is more flexible and scalable for larger applications. AWS offers various services to support both approaches. For example, you might start with a single instance, and as traffic increases, you can increase the instance size (vertical scaling) or add more instances to a load balancer (horizontal scaling). The choice depends on the application’s architecture and expected growth patterns. Consider factors like application design, database scalability, and network capacity when choosing a scaling strategy.
The Role of Auto Scaling Groups in Managing Server Capacity
Auto Scaling groups automate the process of scaling EC2 instances. They monitor metrics such as CPU utilization, network traffic, or custom metrics, and automatically launch or terminate instances based on predefined policies. This ensures that the application always has the appropriate number of servers to handle the current workload, preventing performance degradation during peak periods and avoiding wasted resources during low-traffic times. Auto Scaling groups can be configured to scale based on various triggers, allowing for precise control over resource allocation. For instance, a policy might be set to add instances when CPU utilization exceeds 80% and remove instances when it falls below 50%. This dynamic adjustment maintains optimal performance and cost efficiency.
Implementation of Load Balancing for High Availability
Load balancing distributes incoming traffic across multiple instances, preventing any single server from becoming overloaded and ensuring high availability. AWS Elastic Load Balancing (ELB) offers several types of load balancers, each suited for different application architectures. Application Load Balancers (ALB) operate at the application layer (Layer 7), enabling routing based on HTTP headers and path, while Classic Load Balancers (CLB) and Network Load Balancers (NLB) operate at the transport layer (Layer 4) and network layer (Layer 3), respectively. By distributing traffic, load balancers prevent single points of failure and improve response times. If one instance fails, the load balancer automatically redirects traffic to healthy instances, maintaining continuous service.
Highly Available Architecture Diagram
This diagram illustrates a highly available architecture using several AWS services.
[Diagram Description:] The diagram depicts a multi-tier application architecture. The user’s requests are initially directed to an Application Load Balancer (ALB). The ALB distributes traffic across multiple EC2 instances running the application. These instances are part of an Auto Scaling group, allowing for automatic scaling based on demand. Each EC2 instance is configured to store its session data in a distributed NoSQL database like Amazon DynamoDB, ensuring high availability and scalability for data storage. A Relational Database Service (RDS) instance, potentially a multi-AZ deployment, handles persistent data storage. The RDS instance is protected by a security group restricting access only to the application servers. Amazon S3 is used for storing static content such as images and CSS files. Amazon CloudWatch monitors the entire system, providing metrics and logs for performance analysis and troubleshooting. All components are deployed across multiple Availability Zones (AZs) within a region to further enhance high availability and fault tolerance. In case of an AZ failure, the system automatically routes traffic to healthy AZs. This architecture leverages multiple layers of redundancy to ensure continuous application availability and scalability.
AWS Cloud Server Monitoring and Logging
Effective monitoring and logging are crucial for maintaining the performance, security, and availability of your AWS cloud server environment. A robust strategy allows for proactive identification of issues, efficient troubleshooting, and compliance with security and operational best practices. This section details key metrics, tools, and strategies for implementing a comprehensive monitoring and logging solution within AWS.
Key Metrics for Monitoring AWS Cloud Server Performance
Understanding which metrics to monitor is the foundation of effective performance management. Critical metrics fall into several categories: CPU utilization, memory usage, disk I/O, network traffic, and application-specific metrics. High CPU utilization, for example, could indicate a poorly optimized application or insufficient server resources. Similarly, consistently high disk I/O might point to a need for faster storage. Monitoring these metrics provides early warning signs of potential problems, allowing for proactive intervention before performance degradation impacts users. The specific metrics you choose will depend heavily on the application running on your server.
Using Amazon CloudWatch for Monitoring and Alerting
Amazon CloudWatch is a fully managed monitoring and observability service. It collects and tracks various metrics from your AWS resources, including EC2 instances, databases, and other services. You can configure CloudWatch to collect custom metrics specific to your application, allowing for a highly granular view of its performance. CloudWatch also provides powerful alerting capabilities. You can set thresholds for key metrics and receive notifications (via email, SMS, or SNS) when those thresholds are breached. For instance, an alert could be triggered if CPU utilization exceeds 80% for a sustained period, prompting investigation and potential scaling actions. CloudWatch dashboards provide a centralized view of your metrics, simplifying monitoring and analysis. Visualizations like graphs and charts make it easy to identify trends and anomalies.
Using Amazon CloudTrail for Auditing and Logging
Amazon CloudTrail is a service that provides a record of API calls made to your AWS account. This includes actions performed through the AWS Management Console, AWS SDKs, command-line tools, and other AWS services. This audit trail is invaluable for security monitoring, compliance auditing, and troubleshooting. CloudTrail logs can reveal unauthorized access attempts, configuration changes, and other potentially problematic events. For example, if a security incident occurs, CloudTrail logs can help pinpoint the source and extent of the compromise. CloudTrail data can be integrated with other security tools for enhanced analysis and threat detection. You can configure CloudTrail to deliver logs to an S3 bucket for long-term storage and analysis.
Designing a Comprehensive Monitoring and Logging Strategy for an AWS Cloud Server Environment
A comprehensive strategy involves a combination of tools and best practices. This includes defining key performance indicators (KPIs) based on business needs, establishing appropriate alert thresholds, and implementing automated responses to critical events. This strategy should also incorporate logging of application-specific events, security-related actions, and system-level activities. Regular review and refinement of the monitoring and logging strategy is crucial to ensure its continued effectiveness. For example, as your application evolves and scales, you’ll likely need to adjust the metrics you monitor and the thresholds you set for alerts. Consider using a centralized logging system, such as Amazon Elasticsearch Service, to aggregate logs from multiple sources for easier analysis and reporting. This ensures a holistic view of your AWS environment’s performance and security.
AWS Cloud Server Networking Concepts
Effective networking is crucial for the performance, security, and scalability of any AWS cloud deployment. Understanding the available networking options and how to configure them securely is essential for building robust and reliable cloud-based applications. This section details the core networking components within AWS and illustrates their implementation in a secure architecture.
AWS Networking Options
AWS provides a range of networking services to support various deployment needs. These options offer flexibility in terms of control, security, and cost. Key choices include Amazon Virtual Private Cloud (VPC), Direct Connect, and Transit Gateway. VPC provides isolated network environments within AWS, while Direct Connect establishes a dedicated connection to your on-premises network. Transit Gateway allows you to connect multiple VPCs and on-premises networks.
Virtual Private Clouds (VPCs), Subnets, and Routing Tables
A Virtual Private Cloud (VPC) is a logically isolated section of the AWS Cloud, allowing you to create a virtual network environment dedicated to your resources. Within a VPC, you define subnets, which are ranges of IP addresses within the VPC. Routing tables determine how network traffic flows within the VPC and to the internet. They map subnets to specific network gateways (like internet gateways or NAT gateways). This allows for controlled access to the internet and other AWS services. For example, a subnet might be dedicated to web servers and configured to route internet traffic through an internet gateway, while another subnet housing databases might have restricted internet access.
VPN Connections for Secure Access
To securely connect your on-premises network to your AWS VPC, you can establish a Virtual Private Network (VPN) connection. This creates an encrypted tunnel between your network and your VPC, allowing secure access to resources within the VPC. AWS offers two main VPN connection types: Site-to-Site VPN and Client VPN. Site-to-Site VPN connects your entire on-premises network to your VPC, while Client VPN allows individual users to connect securely to the VPC. Implementing a VPN ensures that all communication between your on-premises network and your AWS resources is encrypted, protecting sensitive data from unauthorized access.
Secure VPC Setup Network Diagram
The following describes a network diagram illustrating a secure VPC setup.
The diagram depicts a single VPC divided into three private subnets (Subnet A, Subnet B, Subnet C) and two public subnets (Public Subnet A, Public Subnet B). Each subnet is associated with a routing table. The private subnets are not directly connected to the internet and utilize a NAT Gateway for outbound internet access. A bastion host, located in one of the public subnets, provides a secure entry point for managing resources in the private subnets. A Site-to-Site VPN connection securely connects the VPC to an on-premises network. Security groups are implemented on all resources to control inbound and outbound traffic. Finally, a network ACL (NACL) further restricts traffic at the subnet level. The diagram visually represents the flow of traffic, highlighting the secure separation between public and private subnets, the use of NAT Gateways, and the secured connection to the on-premises network. This design minimizes the attack surface by restricting direct internet access to private subnets, ensuring that only authorized traffic can reach sensitive resources. The bastion host allows for secure management access while adhering to the principle of least privilege. The combination of security groups, NACLs, and VPN connections provides multiple layers of security, enhancing the overall security posture of the AWS environment.
AWS Cloud Server Backup and Recovery
Data loss can severely impact business operations, rendering systems unusable and potentially leading to significant financial losses. A robust backup and recovery plan is crucial for maintaining business continuity and ensuring data availability in the event of unforeseen circumstances. This section details best practices for backing up AWS EC2 instances, utilizing Amazon EBS snapshots and backups, and designing disaster recovery strategies.
Best Practices for Backing Up AWS EC2 Instances
Regular and automated backups are essential. Consider implementing a backup strategy that aligns with your Recovery Time Objective (RTO) and Recovery Point Objective (RPO). These metrics define the acceptable downtime and data loss in a recovery scenario. A well-defined schedule, such as daily or hourly backups, should be established based on your data sensitivity and change frequency. Furthermore, backups should be stored in a geographically separate region to protect against regional outages. Employing versioning ensures multiple backup copies are available, allowing for rollback to previous versions if necessary. Finally, regular testing of the backup and recovery process is vital to validate its effectiveness and identify any potential weaknesses.
Using Amazon EBS Snapshots and Backups
Amazon EBS (Elastic Block Store) snapshots are point-in-time copies of your EBS volumes. They provide a cost-effective method for backing up your instance’s persistent data. Snapshots are incremental, meaning only changed data is stored after the initial full snapshot. This optimizes storage costs and backup times. For increased protection, consider using Amazon EBS snapshots in conjunction with Amazon S3 (Simple Storage Service) for offsite storage and long-term archiving. Amazon S3 offers various storage classes, such as Glacier, allowing for cost-optimized storage of less frequently accessed backups. Remember to configure appropriate permissions and access controls to secure your snapshots and backups within S3.
Disaster Recovery Strategies for AWS Cloud Servers
A comprehensive disaster recovery plan should incorporate multiple strategies to mitigate various failure scenarios. One approach is to utilize a geographically redundant architecture, where your applications and data are replicated across multiple Availability Zones (AZs) or even regions. This ensures high availability and business continuity in the event of a regional outage. Another strategy is to leverage AWS services such as AWS Elastic Beanstalk or AWS OpsWorks to automate the deployment and management of your applications across multiple regions. This simplifies the process of failing over to a secondary region in the event of a disaster. Regular disaster recovery drills are crucial to test the effectiveness of your plan and identify areas for improvement. These drills should simulate various failure scenarios, including complete regional outages, to ensure your team is adequately prepared.
Designing a Robust Backup and Recovery Plan for an AWS Cloud Server Environment
A robust backup and recovery plan should incorporate the following elements: A clearly defined RTO and RPO, specifying acceptable downtime and data loss; a comprehensive backup schedule that aligns with your RTO and RPO; a strategy for storing backups in a geographically separate region for disaster recovery; a mechanism for automating the backup process; a defined process for testing the backup and recovery process; a documented recovery procedure that Artikels the steps to restore systems and data in the event of a failure; and regular review and updates to the plan to account for changes in your infrastructure and applications. Consider using AWS services such as AWS Backup to simplify and automate the backup process. This service integrates with other AWS services, providing a centralized solution for managing your backups.
Comparing AWS Cloud Servers with Other Cloud Providers
Choosing the right cloud provider for your server needs involves careful consideration of various factors. This section compares Amazon Web Services (AWS) Elastic Compute Cloud (EC2), Google Compute Engine (GCE), and Microsoft Azure Virtual Machines (VMs), highlighting key differences in pricing, features, and performance to aid in informed decision-making. Each platform offers a unique set of strengths and weaknesses, catering to different business needs and technical preferences.
AWS EC2, Google Compute Engine, and Azure Virtual Machines: A Feature Comparison
The following table summarizes the key features of AWS EC2, Google Compute Engine, and Azure Virtual Machines. Note that pricing is highly dynamic and depends on factors such as instance type, region, and usage. This comparison provides a general overview and should be considered a starting point for more detailed research based on specific requirements.
| Feature | AWS EC2 | Google Compute Engine | Azure Virtual Machines |
|---|---|---|---|
| Pricing Model | Pay-as-you-go, reserved instances, savings plans. Offers a wide range of instance types and pricing options. | Pay-as-you-go, sustained use discounts. Provides various machine types with flexible pricing structures. | Pay-as-you-go, reserved instances, Azure Hybrid Benefit. Offers a comparable range of VM sizes and pricing models. |
| Compute Options | Extensive range of instance types optimized for various workloads (compute-optimized, memory-optimized, etc.). Offers specialized instances for specific needs like GPU computing or high-performance computing. | Provides a diverse selection of machine types catering to various computational demands. Offers custom machine types for highly specific requirements. | Offers a broad spectrum of VM sizes, including specialized VMs for data science, AI, and high-performance computing. Provides flexibility in configuring resources. |
| Storage Options | Integrates seamlessly with Amazon S3, EBS, and other storage services. Offers various storage tiers for different performance and cost requirements. | Integrates with Google Cloud Storage, Persistent Disk, and other storage solutions. Offers various storage classes and performance levels. | Integrates with Azure Blob Storage, Azure Files, and Azure Disks. Offers various storage tiers and performance options. |
| Networking | Utilizes Amazon Virtual Private Cloud (VPC) for secure and isolated networks. Offers various networking features like load balancing and VPN connections. | Leverages Virtual Private Cloud (VPC) for secure networking. Offers various networking features like load balancing and VPN connections. | Utilizes Azure Virtual Network (VNet) for secure and isolated networks. Provides features like load balancing, VPN, and ExpressRoute connections. |
| Management Tools | Provides a comprehensive suite of management tools through the AWS Management Console and AWS CLI. Offers robust monitoring and logging capabilities. | Offers a user-friendly console and command-line interface for managing resources. Provides monitoring and logging services through Google Cloud Operations Suite. | Provides a comprehensive management portal and Azure CLI. Offers robust monitoring and logging capabilities through Azure Monitor. |
| Global Infrastructure | Extensive global network of data centers providing low latency access to users worldwide. | Significant global presence with data centers across multiple regions. | Large global footprint with data centers in numerous regions worldwide. |
Advantages and Disadvantages of Each Platform
Each platform presents unique advantages and disadvantages. The optimal choice depends heavily on specific needs and priorities.
AWS EC2: Advantages include its mature ecosystem, vast feature set, and extensive community support. Disadvantages can include the complexity of its extensive offerings and potentially higher costs compared to competitors for certain workloads.
Google Compute Engine: Advantages include its strong focus on scalability and performance, particularly for data-intensive applications. Disadvantages might include a potentially steeper learning curve for users unfamiliar with Google Cloud Platform’s specific tools and services.
Azure Virtual Machines: Advantages include its strong integration with other Microsoft services and its competitive pricing for specific workloads. Disadvantages may include a potentially less extensive community compared to AWS and a potentially more limited range of specialized instance types in certain niches.
AWS Cloud Server Use Cases
AWS cloud servers offer a highly scalable and flexible infrastructure solution, making them suitable for a wide range of applications across diverse industries. Their versatility stems from the ability to easily adjust computing resources based on demand, reducing upfront costs and improving operational efficiency. This adaptability translates to significant benefits for businesses of all sizes.
The inherent scalability and flexibility of AWS cloud servers are key drivers behind their widespread adoption. Businesses can easily scale their computing resources up or down as needed, responding dynamically to fluctuating workloads and avoiding the over-provisioning often associated with on-premise infrastructure. This agility allows for rapid innovation and faster time-to-market for new products and services.
E-commerce and Retail
AWS cloud servers are integral to the success of many e-commerce platforms. They provide the necessary computing power and scalability to handle peak traffic during sales events like Black Friday or Cyber Monday. Companies leverage AWS to manage online stores, process transactions securely, and personalize customer experiences. For example, a rapidly growing online retailer can easily scale its server capacity during promotional periods to avoid website crashes and ensure a smooth shopping experience for customers. The ability to quickly add or remove computing resources minimizes downtime and maximizes sales opportunities.
Media and Entertainment
The media and entertainment industry relies heavily on cloud computing for streaming services, video editing, and content delivery. AWS cloud servers provide the processing power needed for encoding and transcoding high-resolution video, allowing for seamless streaming to millions of users simultaneously. Furthermore, they facilitate collaborative workflows for teams working on large-scale projects, such as film production and post-production. A major streaming service, for instance, might use AWS to handle the massive data volume associated with video storage, delivery, and content management, ensuring a high-quality viewing experience for its subscribers.
Healthcare
The healthcare industry uses AWS cloud servers for various applications, including electronic health record (EHR) management, genomic sequencing, and medical imaging analysis. The secure and scalable nature of AWS allows healthcare providers to store and process sensitive patient data while complying with strict regulatory requirements. For example, a large hospital system can use AWS to store and manage patient records securely, ensuring data privacy and accessibility for authorized personnel. The scalability of the platform allows them to easily handle increasing data volumes as the hospital grows.
Financial Services
Financial institutions utilize AWS cloud servers for high-performance computing tasks, such as risk management, fraud detection, and algorithmic trading. The reliability and security features of AWS are crucial for ensuring the integrity and confidentiality of financial data. A major bank, for instance, might employ AWS to power its real-time fraud detection system, analyzing vast amounts of transaction data to identify suspicious activity and prevent financial losses. The platform’s high availability ensures continuous operation, minimizing disruption to critical financial services.
List of AWS Cloud Server Use Cases with Examples
The following list provides further examples of how AWS cloud servers are utilized across various sectors:
- Gaming: Hosting massively multiplayer online games (MMOGs), providing scalable infrastructure to handle thousands of concurrent players.
- Education: Delivering online learning platforms, supporting virtual classrooms, and providing access to educational resources.
- Government: Managing citizen data, improving public services, and enhancing national security initiatives.
- Manufacturing: Analyzing sensor data from industrial equipment, optimizing production processes, and predicting equipment failures.
- Agriculture: Analyzing data from precision farming technologies, optimizing crop yields, and managing resources efficiently.
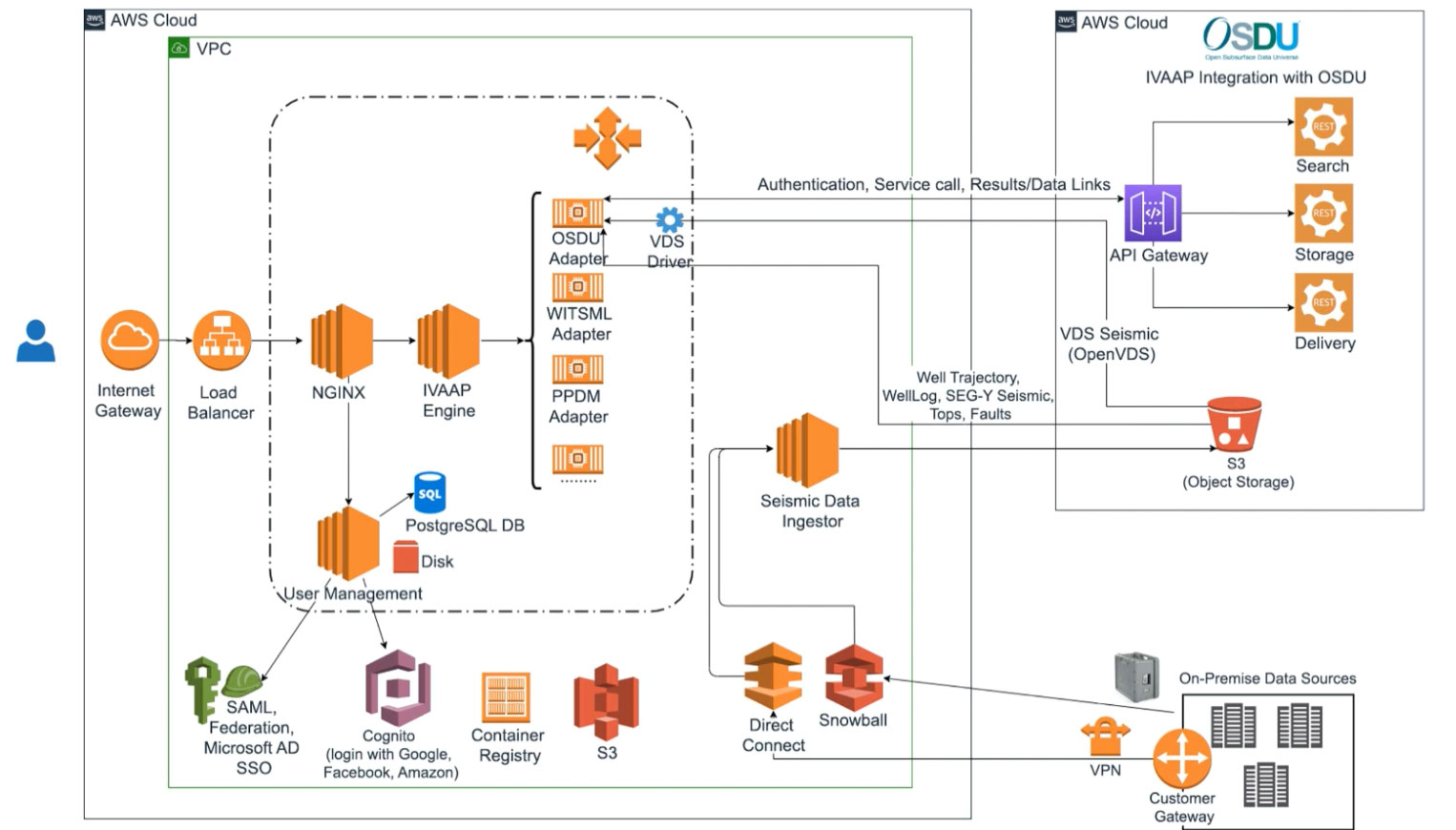
AWS Cloud Server Integration with Other AWS Services
AWS cloud servers, primarily offered through Amazon EC2 (Elastic Compute Cloud), are not isolated entities. Their true power lies in their seamless integration with a vast ecosystem of other AWS services. This integration simplifies application development, enhances security and scalability, and ultimately reduces operational overhead. This section explores how AWS cloud servers interact with other services, focusing on the benefits and providing a practical example.
The integration capabilities of EC2 instances significantly improve the efficiency and robustness of cloud-based applications. By leveraging the interconnectivity between EC2 and other AWS services, developers can build more complex and sophisticated systems without the need for extensive custom integration work. This interoperability is a key advantage of the AWS ecosystem, allowing for a streamlined and efficient development workflow.
Integration with Amazon S3 (Simple Storage Service)
Amazon S3 provides object storage for various data types, including images, videos, and application data. EC2 instances can easily access and store data in S3 using the AWS SDKs (Software Development Kits) available for numerous programming languages. This integration allows for efficient data storage, retrieval, and management. Applications running on EC2 can leverage S3 for persistent storage, backups, and archiving, freeing up EC2 instance storage for operational needs. For instance, a web application running on an EC2 instance might store user-uploaded images in S3, allowing for scalable storage and easy access to these assets. The benefits include cost optimization (paying only for storage used) and high availability (S3 is designed for redundancy and durability).
Integration with Amazon RDS (Relational Database Service)
Amazon RDS manages and scales relational database instances, such as MySQL, PostgreSQL, and Oracle. EC2 instances can connect to RDS instances using standard database connection protocols, allowing applications running on EC2 to interact with structured data stored in the database. This eliminates the need for managing the underlying database infrastructure, simplifying application development and maintenance. The advantages include automatic backups, high availability through multi-AZ deployments, and scalability to handle fluctuating database loads. A common scenario is an e-commerce application running on EC2 that uses RDS to store product information, customer data, and order details.
Enhancing Security and Scalability through AWS Service Integration
Integrating EC2 with other AWS services significantly enhances security and scalability. For example, using AWS Identity and Access Management (IAM) allows fine-grained control over access to EC2 instances and other resources, enhancing security. AWS CloudTrail logs API calls made to AWS services, providing a comprehensive audit trail for security monitoring and compliance. Furthermore, integrating with AWS Auto Scaling allows for automatic scaling of EC2 instances based on demand, ensuring high availability and responsiveness to fluctuating workloads. Using AWS Elastic Load Balancing distributes traffic across multiple EC2 instances, improving application resilience and performance.
EC2 Instance Integration Scenario: A Web Application
Consider a web application deployed across multiple EC2 instances behind an Elastic Load Balancer (ELB). User requests are routed to the EC2 instances through the ELB. The application stores user data in an Amazon RDS database. User-uploaded images and other static content are stored in Amazon S3. Logging and monitoring are handled through Amazon CloudWatch and Amazon CloudTrail. In this scenario, the application leverages the integrated services to achieve high availability, scalability, and security. The ELB distributes traffic, ensuring no single point of failure. RDS provides a reliable and scalable database solution. S3 provides scalable storage for static content. CloudWatch monitors the application’s performance, and CloudTrail provides an audit trail of all API calls. IAM controls access to all resources, enhancing security. This demonstrates the powerful synergy created by integrating EC2 with other AWS services.
Troubleshooting Common AWS Cloud Server Issues
AWS cloud servers, while robust and reliable, can occasionally experience issues. Understanding common problems and their solutions is crucial for maintaining optimal performance and minimizing downtime. This section provides a troubleshooting guide covering network connectivity, performance bottlenecks, and other frequently encountered challenges.
Network Connectivity Problems
Network connectivity issues are among the most common problems encountered with AWS cloud servers. These issues can range from simple configuration errors to more complex network outages. Effective troubleshooting requires a systematic approach, starting with the most basic checks and progressing to more advanced diagnostics.
- Problem: Instance unable to connect to the internet.
- Solution: Verify the security group rules allow inbound traffic on port 80 (HTTP) and 443 (HTTPS). Check the instance’s network interface (ENI) for an assigned public IP address. Ensure the instance’s routing table correctly directs traffic to the internet gateway. If using a NAT gateway, confirm it’s correctly configured and has sufficient capacity.
- Problem: Instances within a VPC cannot communicate with each other.
- Solution: Ensure the security groups associated with the instances allow communication on the necessary ports. Check the VPC’s routing tables to ensure they are correctly configured for intra-VPC communication. Verify that Network Address Translation (NAT) is correctly configured if required for private IP addresses to communicate with the internet.
- Problem: High latency or packet loss.
- Solution: Use AWS tools like CloudWatch to monitor network performance metrics. Identify potential bottlenecks by analyzing latency and packet loss. Consider using AWS Global Accelerator to improve network performance across multiple regions. Analyze network traces using tools like tcpdump to pinpoint specific network issues.
Performance Bottlenecks
Slow performance can stem from various sources, including insufficient compute resources, I/O bottlenecks, or application-level inefficiencies. Identifying the root cause is critical for effective resolution.
- Problem: High CPU utilization leading to slow application response times.
- Solution: Monitor CPU utilization using CloudWatch. Consider increasing the instance size to provide more CPU cores and memory. Optimize the application code to reduce CPU consumption. Use Amazon RDS Performance Insights to identify database queries impacting performance.
- Problem: Slow disk I/O impacting application performance.
- Solution: Monitor disk I/O using CloudWatch. Consider using faster storage options like EBS io1 or gp3 volumes. Optimize the application’s database design and queries to reduce disk I/O. Use EBS optimization for better performance.
- Problem: Memory leaks or inefficient memory usage.
- Solution: Use memory profiling tools to identify memory leaks or inefficient memory usage within the application. Optimize the application code to reduce memory consumption. Increase the instance size to provide more memory.
Troubleshooting Guide: Common Problems and Solutions
This section summarizes common problems and their corresponding solutions for easy reference.
| Problem | Solution |
|---|---|
| Instance not starting | Check instance status in the console, verify security group rules, and ensure sufficient resources are allocated. |
| Application error | Review application logs, check for resource constraints, and use debugging tools. |
| Database connection issues | Verify database credentials, check network connectivity, and ensure the database is running. |
| Security group issues | Review security group rules to ensure appropriate inbound and outbound traffic is allowed. |
Essential FAQs
What are the different instance types available in AWS EC2?
AWS EC2 offers a wide range of instance types optimized for various workloads, including compute-optimized, memory-optimized, and storage-optimized instances. The choice depends on your specific application requirements.
How do I choose the right AWS region for my server?
Region selection depends on factors like latency requirements for your users, data residency regulations, and pricing. Consider proximity to your target audience and any legal constraints on data location.
What is the difference between a security group and a network ACL?
Security groups act as firewalls for individual instances, while network ACLs control traffic at the subnet level. Security groups are stateful, while network ACLs are stateless.
How can I monitor my AWS cloud server’s performance?
Amazon CloudWatch provides comprehensive monitoring and alerting capabilities. You can track key metrics like CPU utilization, memory usage, and network traffic to identify performance bottlenecks.